What is cloud computing? As Intel founder Gordon Moore once said, "The number of transistors that can be accommodated on integrated circuits will double every two years.". In other words, processor performance doubles every two years. With such rapid development, the cost of hardware is getting lower and lower, and a single enterprise can afford a large number of servers.
CLO
Over the past 20 years, public cloud architectures have transformed the process and approach to software deployment, bringing tremendous convenience and efficiency to customer access to software. However, there are still government and commercial customers who, for a variety of reasons, have to accept private software environments over which they maintain full control.
Security ThreatsWhile most cloud providers have adopted some security measures to prevent hackers from penetrating their cloud infrastructure, the incidence of data breaches indicates that cloud computing remains vulnerable to attack.
Data scientists must move data from central servers to their systems for analysis, a time-consuming and complex process. Cloud computing has revolutionized the way organizations handle data by eliminating the need for physical servers and providing on-demand, scalable resources.
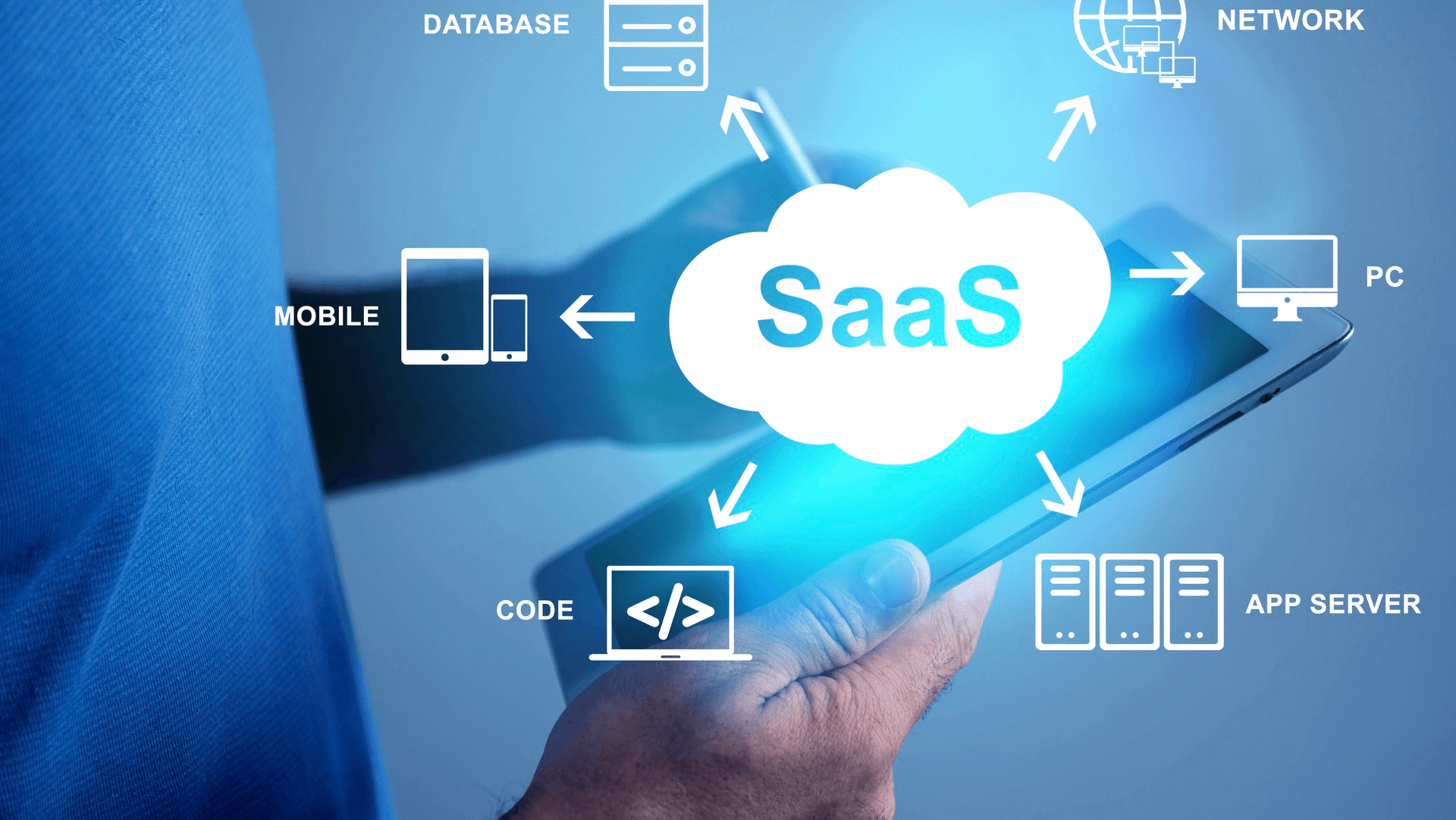
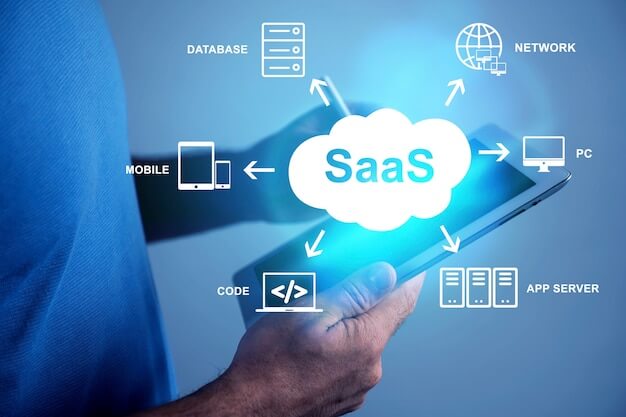
In a business environment, SaaS is an optimal alternative to local services (traditional methods), which require server creation, application installation, and configuration.
Whether it is a public or private cloud, the intended value of the cloud can only be realized if it is used wisely. To make use of cloud computing IT infrastructure more "green", the following seven aspects are very important.
Collaboration tools with cloud connectivity are an important foundation for these optimization processes. With these tools, you can manage the complexity of the supply chain and improve the quality of the final product.
As sustainability becomes a front and center topic for the enterprise, stubborn misconceptions about the power consumption of cloud-based deployments need to be debunked.
Recently, the cloud game market and add a strong competitor, Amazon announced the official entry into the cloud game market, the launch of the Luna service.
When the core of cloud computing system computing and processing is a large amount of data storage and management, the cloud computing system needs to be configured with a large number of storage devices, then the cloud computing system is transformed into a cloud storage system